How to Deploy and Setup HoneyDrop Honeypot in AWS
What
The HoneyDrop appliance is a low-interaction honeypot meant to be deployed in subnets where critical visibility of malicious activities is needed. The HoneyDrop can be configured to emulate:
- Windows SQL servers
- Windows web servers
- Linux MySQL servers
- Linux web servers
When the HoneyDrop appliance is interacted with, alerts are sent to Slack, Discord, and Microsoft Teams. Logs are generated and sent to AWS CloudWatch where they can trigger SNS notifications to send emails, SMS messages or launch Lambda functions.
Why
- Gain visibility into your AWS VPS network environments.
- Enhance security posture without needing to install agents on instances.
- Lure attackers away from high value systems long enough to be identified.
- Enable automated incident response actions to isolate and quarantine compromised hosts.
- Immediate visibility with source IP address and credentials used to interact with the honeypot.
How
The following steps will explain how to setup and deploy the HoneyDrop appliance.
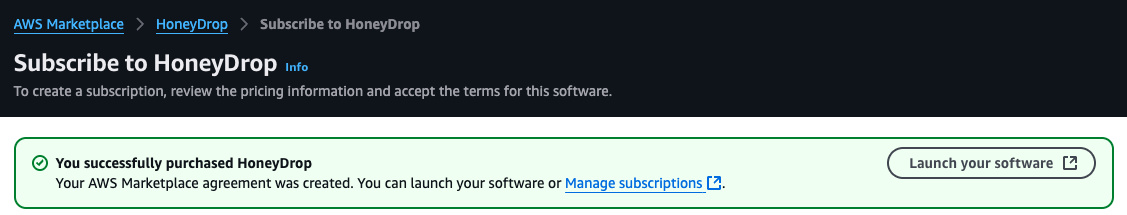
- Subscribe to the HoneyDrop appliance in the AWS marketplace.
- Click "Launch your software".
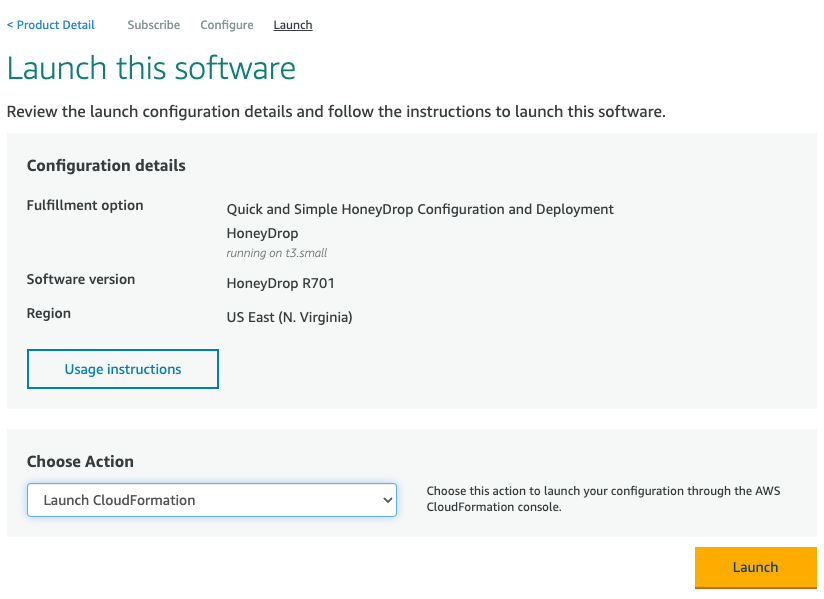
- Validate the region is set correctly and click "Continue to Launch".
- Set the "Choose Action" to Launch CloudFormation and click "Launch"
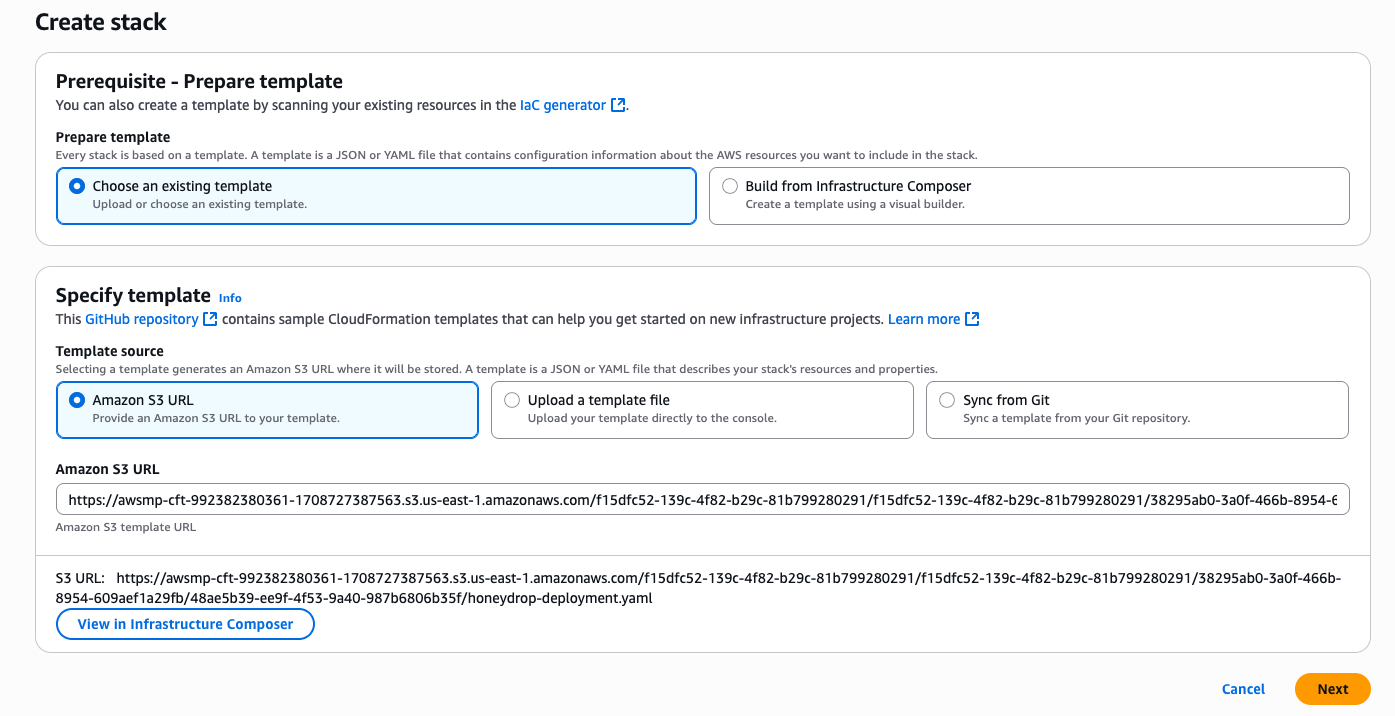
- Once redirected to CloudFormation, click "Next" to begin creating the stack.
- Name the stack "HoneyDrop", and set the honeypot services to "true" that you would like to be enabled. Be sure to also set the following required parameters:
- Optionally, set some tags and click "Next".
- Finally, review the stack and click "Submit".
InstanceType
IsPublicSubnet
KeyPairName
ManagementCIDR
ServicesCIDR
SubnetId
VpcId
NotificationsDiscordUsername
NotificationsDiscordWebhook
NotificationsSlackUsername
NotificationsSlackWebhook
NotificationsTeamsWebhook
Here's a guide for Slack.
Here's a guide for Discord.
Here's a guide for Microsoft Teams.
Now, click "Next".
And that's it! Your appliance should now be up and running in your environment. Test the services you enabled by interacting with them and see the alerts appear in Slack, Discord, Teams, and AWS CloudWatch.
Setting Up CloudWatch Alarms
If desired, you can set up CloudWatch alarms to be triggered when the HoneyDrop appliance catches an attacker. This is a great way to automate your incident response process.
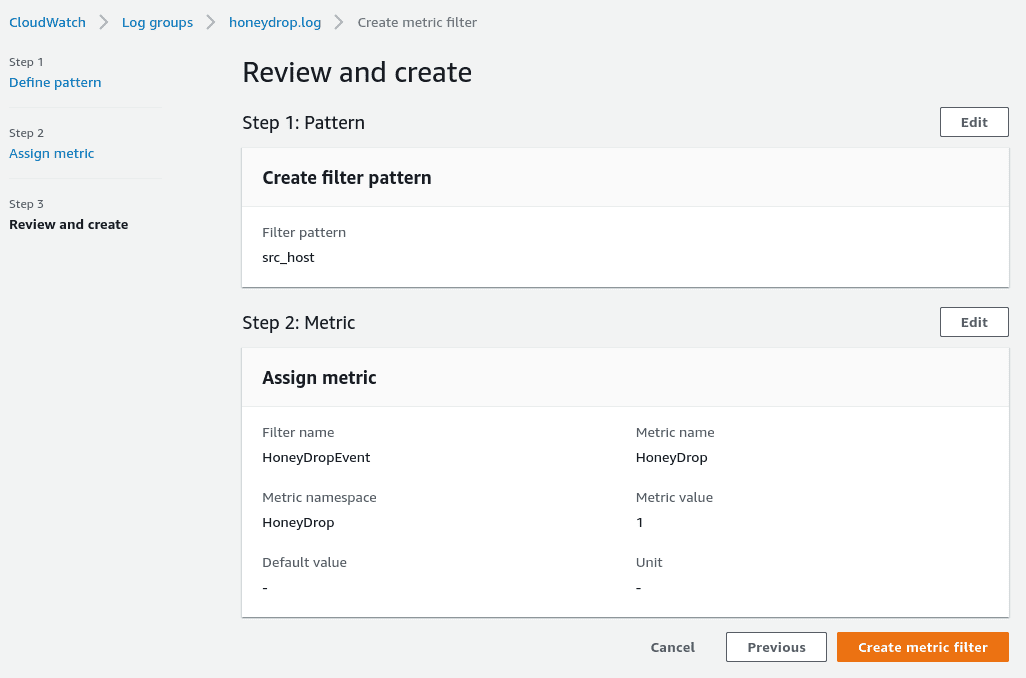
First, let's configure the metric filter within CloudWatch Logs. This is necessary to identify events triggered by the HoneyDrop appliance. AWS does a great job explaining the setup here, but for the sake of simplicity, navigate here and click on "Create Metric Filter".
Here we will set the filter pattern to "src_host". This means that any time an event is recorded, the metric filter will be triggered since all HoneyDrop events capture the source host field in their logs. Set the additional parameters according to the image below.
Next, we need to setup our SNS topic. This is the mechanism that will send an email out whenever the HoneyDrop catches an attacker. We'll start by navigating to AWS Simple Notification Service (SNS) and clicking on "Topics", or just click here. Now, click on "Create topic". Enter the details according to the following image.
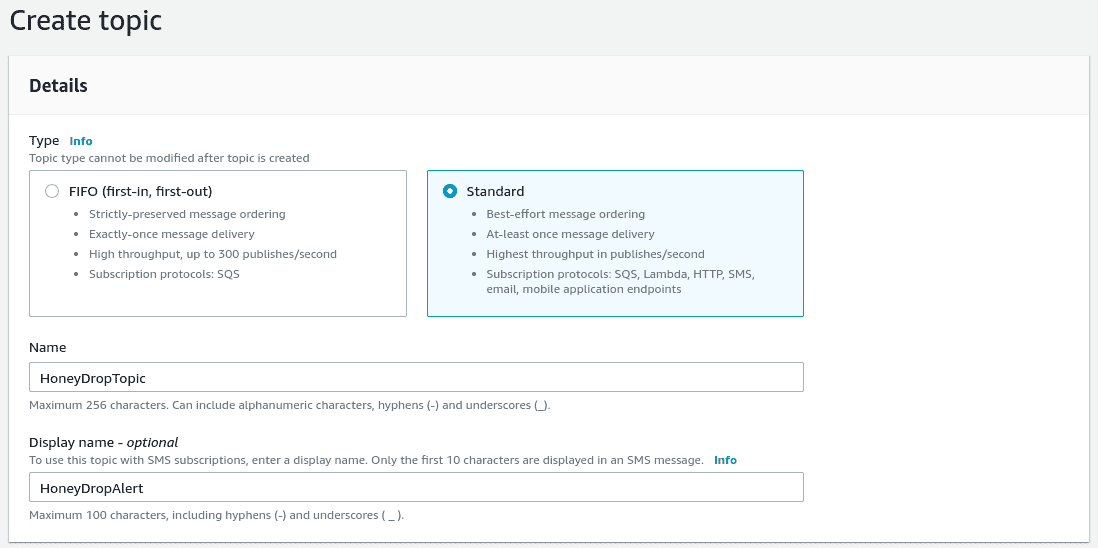
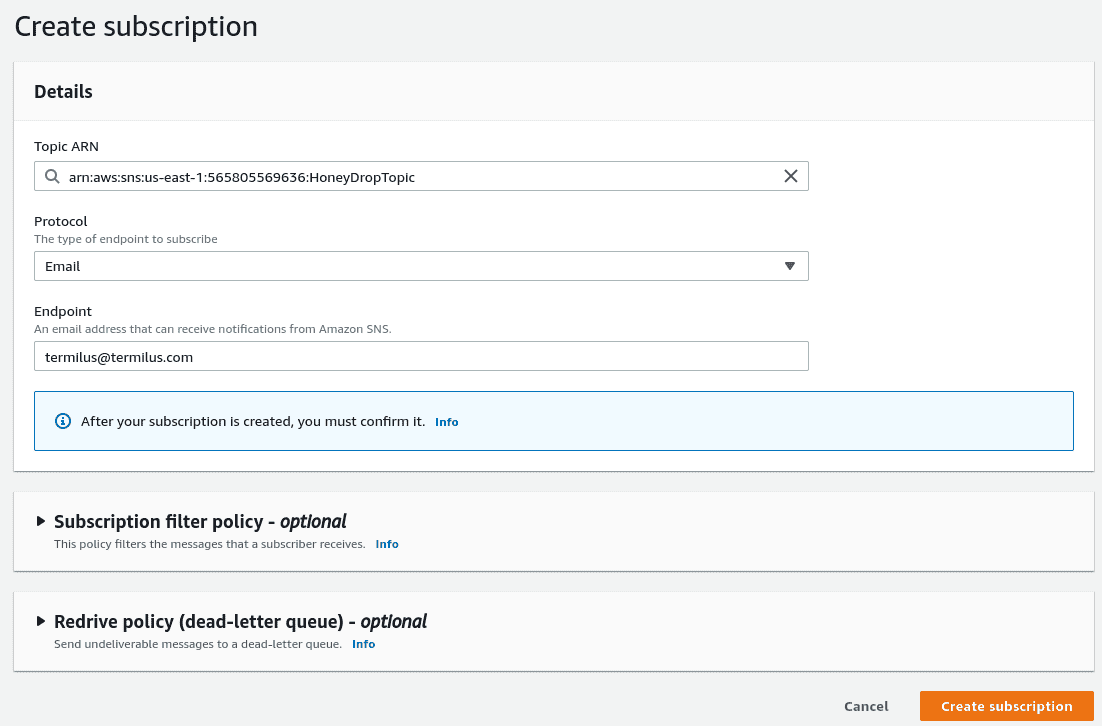
Now we need to subscribe to our topic by clicking on "Create subscription". Set the "Protocol" to email and the "Endpoint" to your email address then click "Create subscription".
Don't forget to check your email and click "Confirm subscription".
Next, we'll configure a CloudWatch alarm. Navigate to the the "All alarms" pane in CloudWatch, here and click "Create alarm" and then "Select metric". Here, we'll select "HoneyDropMetrics", then "Metrics with no dimensions", then check "HoneyDropEvent" and click "Select metric". Now, enter the metric and condition details according to the following images and click "Next".
Now, we'll configure the alarm to send our SNS notification whenever it's triggered. Once our SNS topic is selected, we can hit "Next".
Here, we enter our alarm name and description and hit "next".
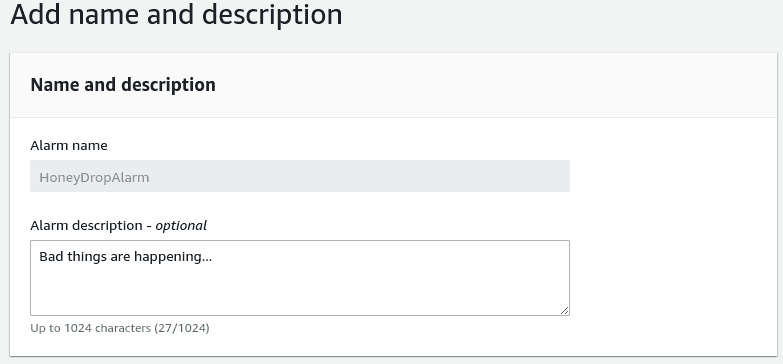
Finally, we can review our alarm and hit "Create alarm".
That's it. Now, whenever our HoneyDrop appliance lures in an attacker, its services will capture the interaction and trigger an SNS email notification - alerting you that bad things are happening.
Troubleshooting
- Not seeing alerts in CloudWatch Logs?
- Check to make sure the HoneyDrop is in a subnet where other hosts can reach it and that security group permits inbound connections on enabled services.
- Ensure the role attached to the HoneyDrop appliance has the CloudWatchAgentServerPolicy policy attached to it.
- Attempt authenticating to one of the enabled services to generate some logs.
FAQ
Does the HoneyDrop appliance support single-AZ, multi-AZ or multi-region deployments?
The appliance is a single EC2 instance that can be deployed into any VPC in any region.
Does the HoneyDrop appliance support all regions?
Yes, all regions are supported.
Should we use the root user for deploying the HoneyDrop appliance?
No, it is recommended to use a non-root user to deploy the appliance.
Should the HoneyDrop appliance be encrypted when deployed?
Yes, security best-practice is to encrypt the appliance when provisioned.
Is data in-transit encrypted?
Yes, data sent to CloudWatch Logs is encrypted in-transit.
Which services used by HoneyDrop are billable?
The HoneyDrop appliance incurs Cloudwatch, EC2, and software cost when deployed. For example, a t3.medium HoneyDrop instance costs $0.042 per hour plus $0.05 per hour for software for a total of $0.092 per hour of deployment.
How can I monitor the health of the HoneyDrop appliance?
Check the health of your server by viewing its status in the "Instance State" column in the EC2 Dashboard.
How does the HoneyDrop appliance get patched and updated?
The appliance is set to auto-install security patches on a daily basis.
How do I handle a non-responsive HoneyDrop appliance?
This is very rare, but a reboot should resolve the issue.
Is there technical assistance available to help troubleshoot?
Yes, we're available to assist and will typically respond within 1 business day. We can be reached by emailing: [email protected]

