Easy Static Application Security Testing with Salient
Estimated Deployment Time
15 Minutes
What
The Salient Static Application Security Testing (SAST) appliance monitors your Github codebase for any new code pushes or merges into a target branch. Once new code has been detected, the appliance runs it through a static application security test to check for any new code vulnerabilities.
If any new vulnerabilities were identified, those vulnerabilities are pushed to a custom Slack or Discord channel. Details of vulnerabilities include:
- Vulnerable file's path
- Type of vulnerability
- Short explanation
- Vulnerable snippet and line number
- Detailed reference hyperlink
Why
SAST scanning plays a crucial role in the Software Development Life Cycle (SDLC) by identifying vulnerabilities early in the development process, long before the software is deployed. By analyzing source code without executing the program, SAST allows developers to detect security flaws, such as coding errors and compliance issues, at a stage where they can be addressed with minimal cost and effort.
Additionally, integrating SAST into the SDLC helps organizations meet regulatory requirements, reduces the risk of costly data breaches, and ultimately builds trust with users by delivering more secure software. Salient's SAST appliance seamless integrates into the SDLC by running out-of-band and publishes its findings to Slack and Discord channels for quick, convenient security feedback.
How
For this tutorial we will deploy the Salient SAST appliance via the AWS marketplace. Next, we'll configure some policies to give the appliance the appropriate permissions to read private Github repositories and allow it to publish to Slack and Discord.
Here is an architectural diagram of what we’ll be setting up:
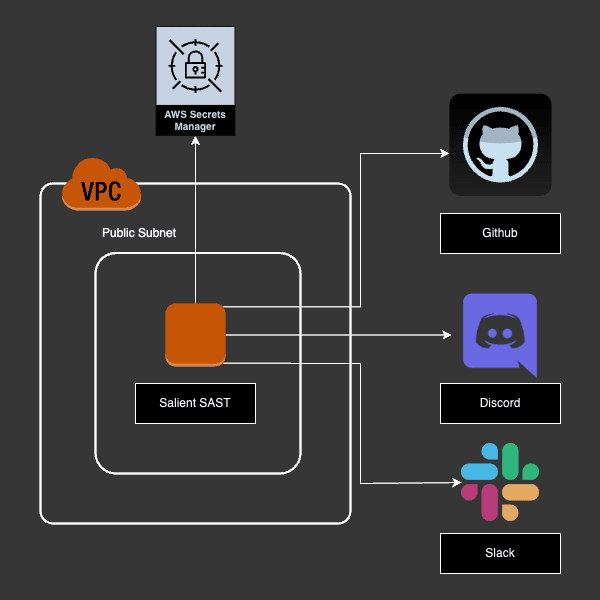
Configure AWS Secrets Manager
- Head over to AWS Secrets Manager and create a new secret, set the type as "other" and enter value pairs for the following keys:
- Discord_Username
- Discord_Webhook
- Slack_Username
- Slack_Webhook
- GitHub_Username
- GitHub_PAT
- Repository
- Branch
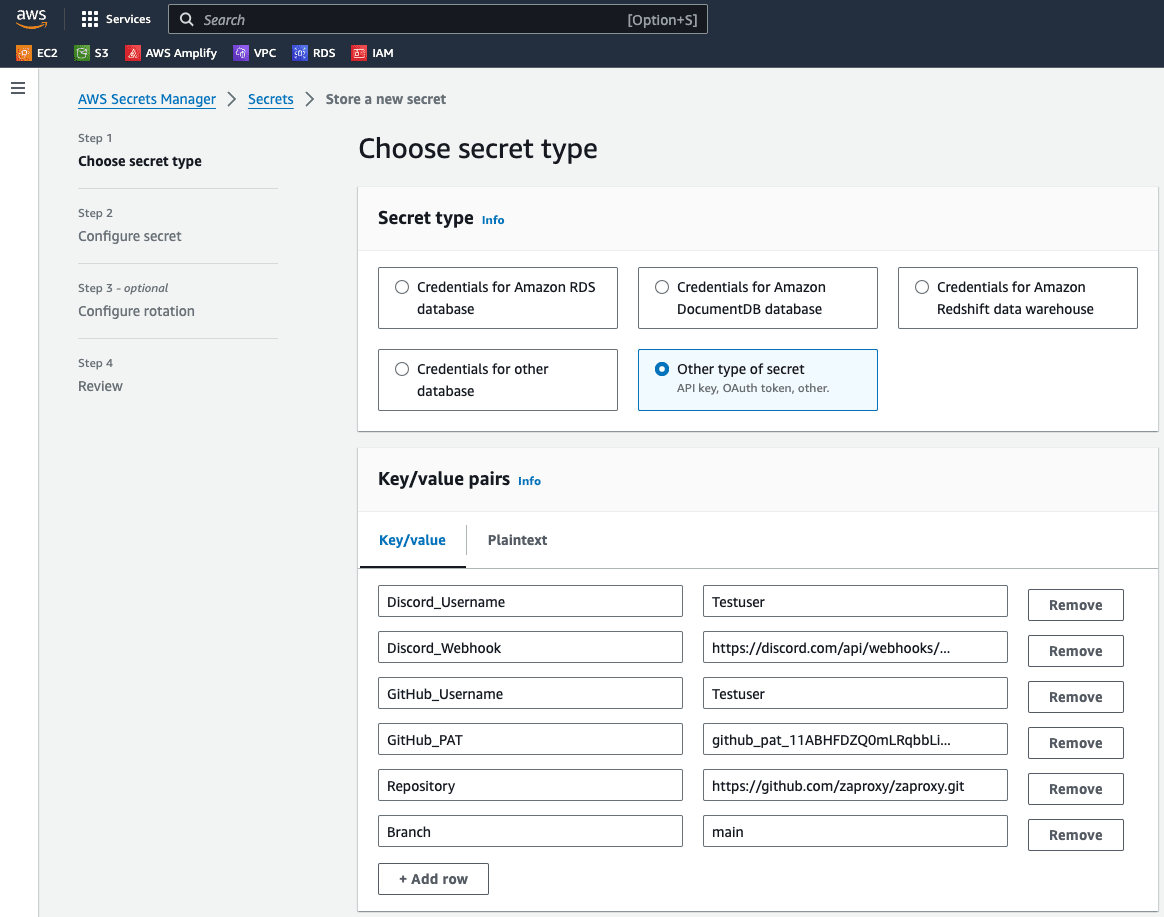
Either or both Slack and Discord usernames and webhooks can be specified. These usernames and webhooks will be used for notifications of new vulnerabilities identified.
Click here to see how to set up a Slack webhook and here to set up a Discord webhook - both are quick and easy.
2. The default encryption key is fine, click next. Set the secret name as "SAST" and enter an optional description.
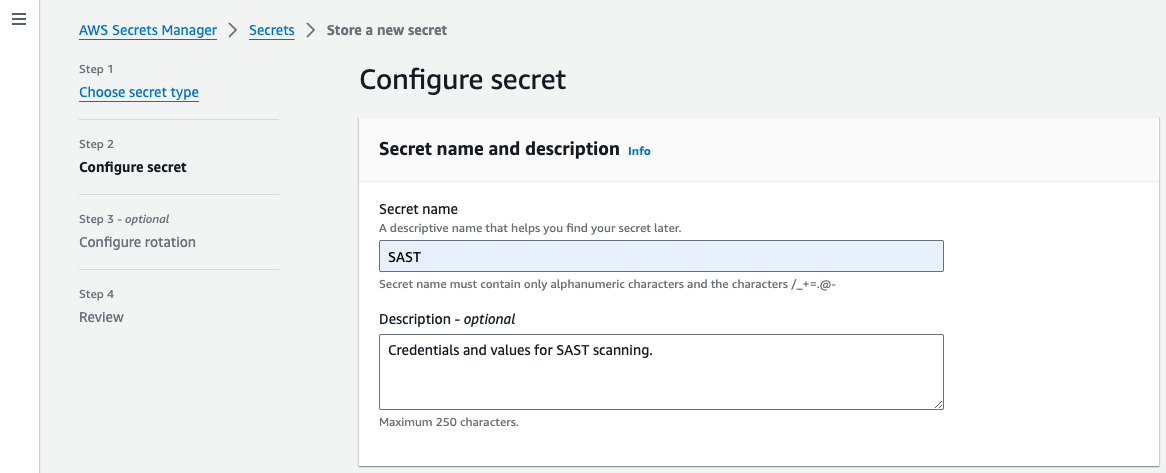
Skip rotating the keys and store it.
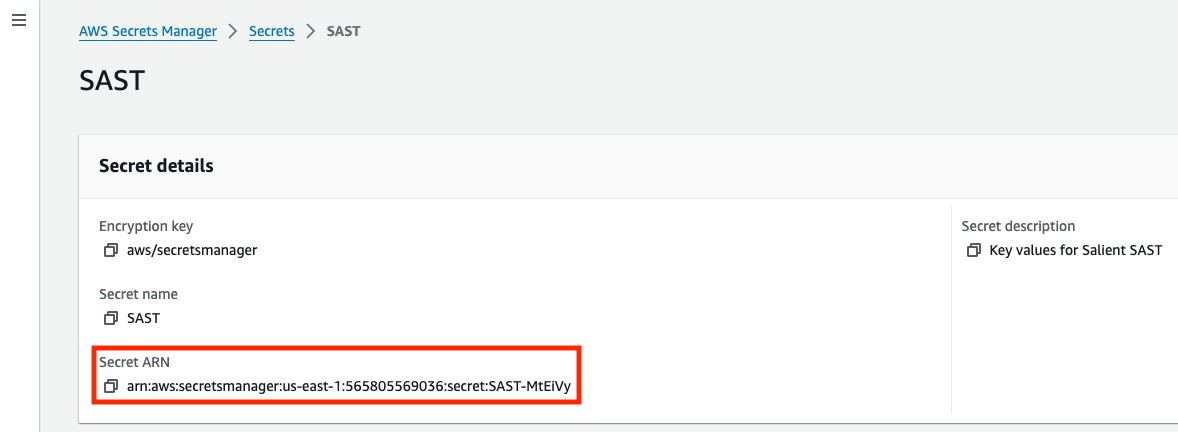
3. Make note of the Secret ARN, you'll need it in the next step:
Configure the IAM policy and role:
- Head over to IAM policies and click "Create policy".
- Select JSON and paste the following JSON code:
{"Version": "2012-10-17","Statement": [{"Effect": "Allow","Action": ["secretsmanager:GetResourcePolicy","secretsmanager:GetSecretValue","secretsmanager:DescribeSecret","secretsmanager:ListSecretVersionIds"],"Resource": ["arn:aws:secretsmanager:us-east-1:565805569036:secret:SAST-MtEiVy"]},{"Effect": "Allow","Action": "secretsmanager:ListSecrets","Resource": "*"}]}
- Make sure to update the Resource to be the proper Secret ARN we grabbed in the last step. Next, give the policy a name like "ReadSecrets" and click "Create policy".
- Now, let's head back to IAM and create a new role to attach the SAST policy to. Click the "Create role" button.
- Set the "Trusted entity type" to be "AWS service". Set the Use case to EC2:
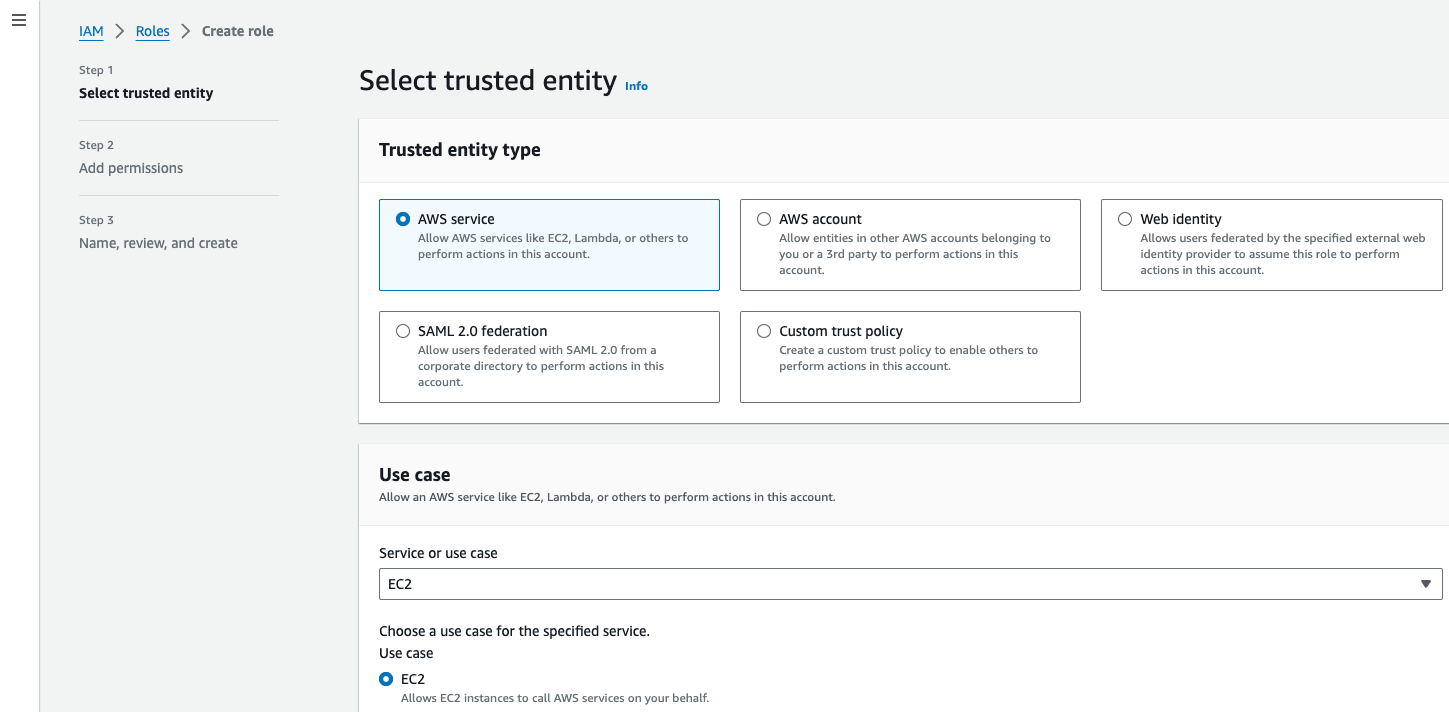
6. Now, click next and search for our ReadSecrets policy. Select it and again, click next.
7. Give the role a name like "SAST" and click "Create role".
How to deploy the Salient SAST appliance:
- Deploy the Salient SAST appliance from the marketplace into your public subnet.
- Back on the EC2 dashboard, locate the SAST instance, right click on it and modify its IAM role:
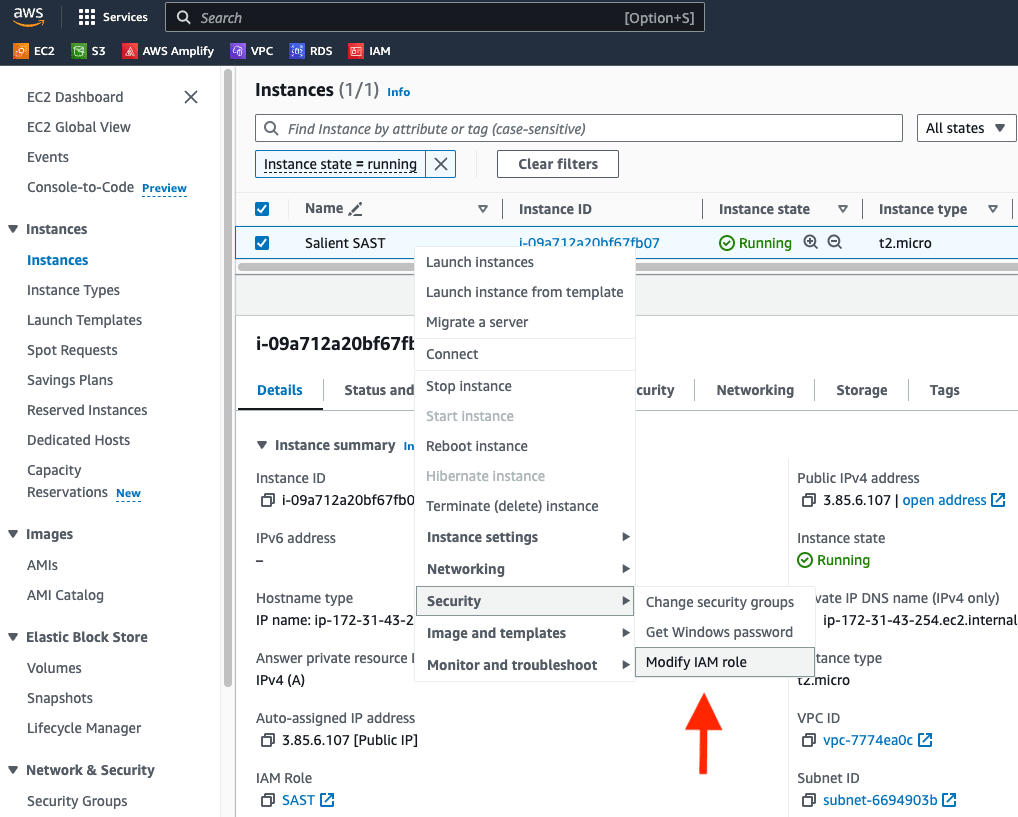
Set the role to our newly created SAST role and click Modify IAM Role.
3. Reboot the SAST EC2 instance.
And that’s it! Your Salient SAST appliance is now monitoring your selected code repository branch for any new code pushed or merged into it. When a new vulnerability is identified, the appliance will send a notification to either or both Slack and Discord with the vulnerability details. Only new vulnerability notifications are sent, and they are only sent once to minimize alert fatigue:
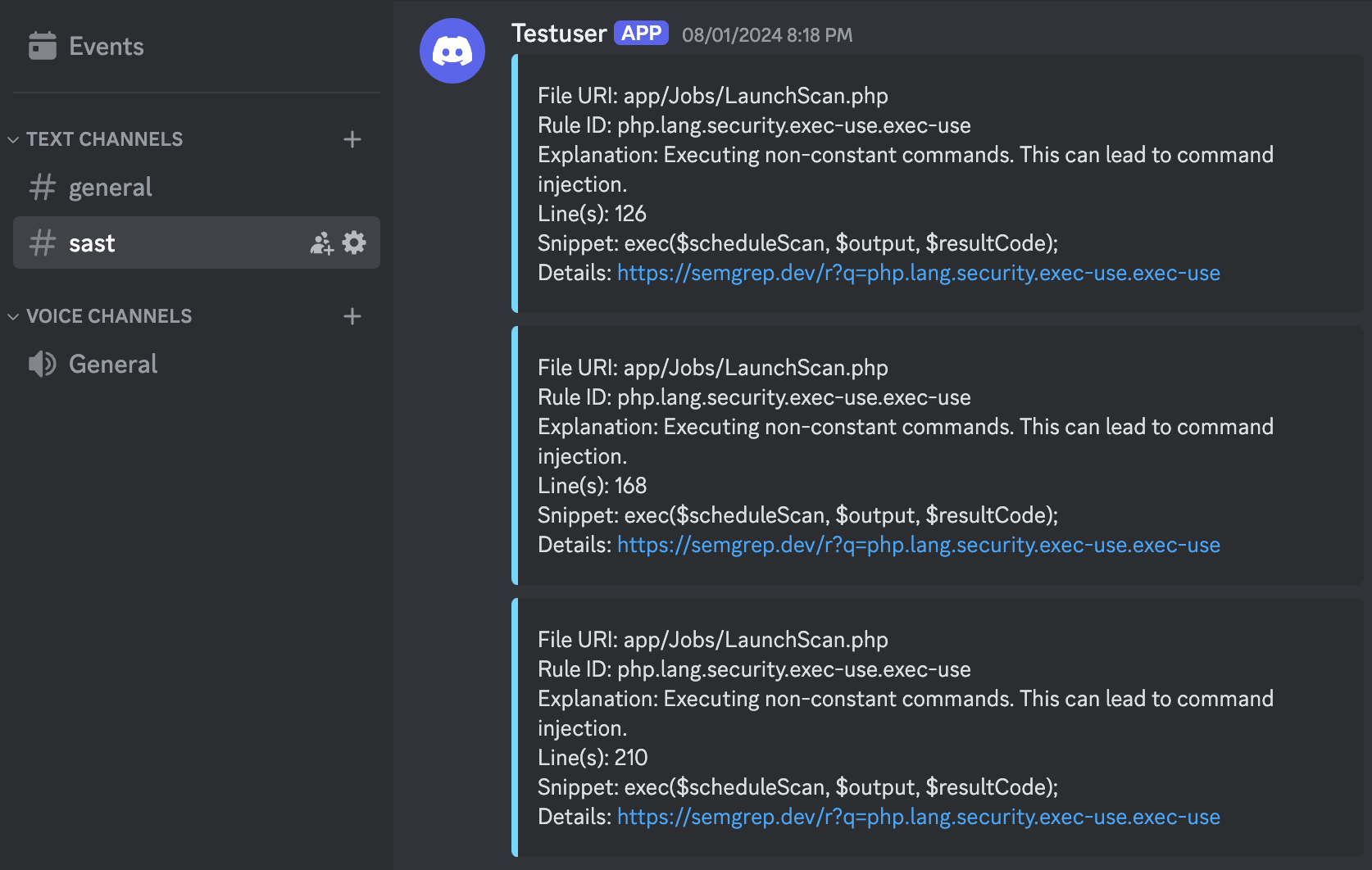
Troubleshooting
No alerts populating in Slack or Discord?
- Check to make sure the SAST IAM policy has the correct secret ARN specified.
- Make sure the IAM role has been applied to the EC2 instance.
- Make sure the secret key names are exactly as specified in this post.
- Make sure the webhooks have been created and are specified in the secrets.
- Make sure the correct branch is specified in the secrets.
- If authentication is required to access a private repository, provision a Github PAT.
Need to see the full SAST report?
- SFTP the file off of the server with the following command.
scp -i ~/.ssh/replacewithyourkey.pem [email protected]://home/ec2-user/scans/semgrep.txt ./semgrep.txt
FAQ:
- Does the Salient SAST support all regions? Yes, all regions are supported.
- Should I use the account root user to deploy this appliance? No, we recommend using a non-root user to deploy this appliance.
- Is encrypted traffic decrypted by the appliance at any point, either in-transit or at rest? No, the Salient SAST appliance never decrypts encrypted traffic.
- Does the Salient SAST appliance require any billable services? Yes, in addition to the appliance subscription, the Salient SAST will incur the cost of the EC2 instance selected. For example, the licensing cost for a t2.micro instance would be $0.02 for the software and $0.012 for the EC2 instance, yielding a total cost of $0.032 per hour.
- How large of an EC2 instance should we deploy? We recommend a t3.medium for most production use cases.
- How can I check the health of my SAST appliance? Check the health of your server by viewing its status in the "Instance State" column in the EC2 Dashboard.
- How can I install system or software patches? Once the system is rebooted, it will auto-install all requisite updates and upgrades.
- How do I handle a non-responsive SAST appliance? This is very rare, but a reboot should resolve the issue.
- Is there technical assistance available to help troubleshoot? Yes, we're available to assist and will typically respond within 1 business day. We can be reached by emailing: support at salientengineering.com
Contact Us
Get in Touch
Have a question about our cloud solutions or need support with your current setup? We're here to help! Fill out the form below, and our team will get back to you as soon as possible to assist with your needs.